As an election official, you’ve likely spent the past four years upgrading systems, patching vulnerabilities, and implementing new security features and procedures to safeguard the 2020 elections. But now, with tens of millions of ballots already cast and vote counting just a week away, you’ve clearly transitioned from the preparation to the execution stage of the elections. It may therefore seem like an inopportune time to talk about election security.
Yet Iran’s attempts last week to intimidate voters in four states using spoofed e-mails shows that work remains to protect the elections, particularly in the information domain. Iran’s efforts to undermine American confidence in the integrity of the elections was a real-world manifestation of several threat warnings from the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) and the FBI that cybercriminals and foreign adversaries, namely Russia, could try to spread disinformation about voter suppression, voter fraud, and election results through new or hacked websites and social media accounts, including those belonging to election officials. And just last night, the Trump campaign’s website was hacked and temporarily defaced. These episodes should serve as canaries-in-the-coal-mine moments and reaffirm the need to take the security of information channels as seriously as the security of election infrastructure.
The good news is that the steps needed to secure election-related information channels require no additional funding, training, or other resources to implement. But it is also important to stress that, amid an election, these suggestions are only best practices if they do not create undue stress for you or your staff.
This caveat aside, here are seven simple steps you can take today to protect the integrity of your information channels, many of which can be accomplished in about the time it takes to brew a fresh pot of coffee.
1. Enable multi-factor authentication on social media accounts
Time Required: Less than 15 minutes
Enabling two-factor or multi-factor authentication is the best way to prevent unauthorized access to your communication channels. Digital authentication adds an extra layer of security in case someone guesses or steals your passwords, minimizing the risk of threat actors using phishing attacks to hijack or deface your website or social media accounts. While multi-factor authentication should be used across all information systems, now is not the time to implement new procedures that may disrupt employees’ access to email and other critical communication channels. However, multi-factor authentication is required to verify your social media accounts (more on the importance of that below), and Facebook and Twitter offer easy solutions to enable two-factor authentication.
2. Change password(s) on key accounts now
Time Required: Less than 5 minutes
If your password or passwords have been compromised without your knowledge, changing your passwords now can root out potential threat actors who may be lurking in your systems. Changing your existing passwords (ideally using a random password generator) does not replace the security of multi-factor authentication, but it does provide additional protection from identity-based intrusions.
3. Verify Your Social Media Pages and Accounts
Time Required: Less than 30 minutes
Most major social media platforms offer the ability to verify an account or page of public interest. Account verification on Twitter and Facebook—often referred to as a blue badge or checkmark—is a simple and free step you can take to secure your official profiles, increasing public confidence in the reliability of information coming from your social media channels. This step also makes it more difficult for bad actors to create spoofed or imposter accounts to mislead voters. In addition, Facebook’s voter information center will prioritize information posted by verified election accounts, meaning that your messages will be elevated above others.
In many cases, your social media accounts may already be eligible for verification. In others, you may only need to make one or two minor updates to make your accounts eligible. ASD has helped many counties navigate the verification process and is happy to help officials who need assistance (email info@securingdemocracy.org).
Below are the verification requirements for Twitter and Facebook.
Twitter verification requires:
- Two-factor login authentication must be enabled
- Registration email must be a government e-mail
- Personalized cover and profile photo (i.e., not Twitter’s default photos)
- Bio must specify the purpose of the agency
- Link to official website
- Account must be active
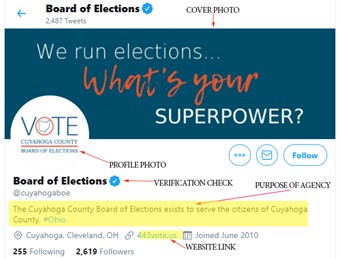
Example of a verified election-related Twitter account
Facebook verification requires:
- Two-factor login authentication must be enabled
- Profile and cover photos have been added
- Link to official website
- Page name must indicate that it represents a government entity and not just a place (e.g., Miami-Dade County Election Department; not Miami-Dade County)
- Page category should only indicate “Government Organization”
- Page CANNOT contain a person’s name, like a county supervisor
- Content must be posted to the page
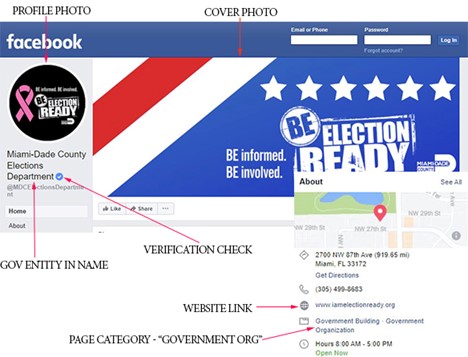
Example of a verified election-related Facebook account
4. Check and update external links
Time Required: Less than 5 minutes
If you have added, removed, or updated your website or social media accounts it is possible that you may have outdated or broken links on one or more of your information channels. At a minimum, broken links will direct the public away from the most accurate and up-to-date information, but they can also be used to re-direct voters to malicious websites. Take five minutes to ensure that the links to your social media accounts on your website are accurate, and vice versa.
5. Search for and deactivate unused or “zombie” accounts
Time Required: Less than 20 minutes
Threat actors can hijack official accounts that are no longer actively being used or monitored. If you have changed a social media profile or simply stopped using an account, take the time to deactivate it. Also, it is a good time to scan social media platforms to see if there are any defunct, spoofed, or otherwise suspicious accounts connected to your agency. Whether these accounts were created for legitimate purposes or not, they present an information security risk and should be deactivated or reported to the relevant platform.
6. Designate personnel to monitor communication channels
Time Required: Less than 5 minutes per day
Counties without a dedicated communications professional or team should designate an individual or individuals to be responsible for their information security. This person or team should know the password to all websites and social media accounts, have up-to-date contact information for relevant support staff (both at the state level and at the platforms), and, at a minimum, actively monitor each channel daily for suspicious activity. As with cyber security, the time to devise an incident response plan is before there is a problem.
7. Post content early and often
Time Required: 10-15 minutes per day
While not technically an information security recommendation, it is essential that election officials establish their accounts as trusted sources of information before, during, and after the election. While the best time to build a following on social media is well before an election, it is not too late to start an aggressive messaging campaign. Whether you are new to social media or a seasoned pro, it takes just a few minutes a day to remind voters of deadlines, polling locations, and other helpful tips to make sure your community is prepared for election day. Remember, bad actors are flooding social media with information meant to undermine confidence in the election, your account should be an antidote to those efforts.
The views expressed in GMF publications and commentary are the views of the author alone.